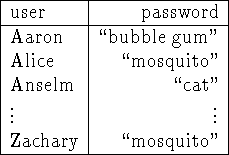
Figure 1: In a straightforward approach to organizing the password file, each entry gives the password of one user.
Consider the use of passwords for restricting access to some resource such as a computer. In a straightforward approach, the computer stores a big table called the password file. Each user is listed in the table along with that user's password. When someone tries to gain access (by logging in), they give their name and password to the computer, and the computer looks up the name in the table and compares the password given to the one recorded in the table under that name. If they match, the computer assumes that the person trying to log in gave their real name, and grants the person access.

Figure 1: In a straightforward approach to organizing the password
file, each entry gives the password of one user.
In such a system, the password file is a weak point in the security of the system. A hacker who somehow manages to gain access to the password file immediately obtains the password of every user of the system and can henceforth impersonate every user. Since people often use the same password for access to multiple systems, this sometimes enables the hacker to break into other computer systems, and so on. This trick was one of those used by the Internet Worm of November 1988, a rogue program that duplicated itself and spread broadly through the Internet.
To make the password file slightly less useful to hackers, a one-way function is used. Along with the name of each user, instead of giving the user's password, the table gives the image of the password under the one-way function. Now when a user tries to log in, supplying her name and password to the system, it applies the one-way function to the password, obtaining the image of the password under that function, and compares that result to the user's entry in the password file. If there is a match, the user is granted access.
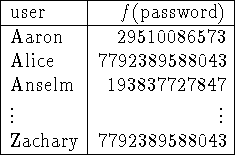
Figure 2: In a more secure system, each entry of the password file
gives the image of the user's password under a fixed one-way function f.
In this example, ![]() and
and
![]() . Note that the same value is
stored under Alice's name and Zachary's name because they happen to
have chosen the same password.
. Note that the same value is
stored under Alice's name and Zachary's name because they happen to
have chosen the same password.
How does this use of a one-way function enhance security? A hacker who gains access to the password file does not thereby obtain passwords for all the users, at least not directly. The definition of a one-way function (namely the fact that it is computationally difficult to ``go backwards'') implies that the hacker cannot easily derive a user's password from the corresponding value stored in the password file.