


Next: Application of one-way functions
Up: Dictionary attack on password
Previous: Dictionary attack on password
This last observation concerning the effectiveness of a dictionary
attack on the password file suggests a technique to hinder a hacker's
attack. The goal is to ensure that each entry in the password file
is specific to the user. When a user's password is to be entered into
the system, an additional number, called the salt, is chosen. The
salt may depend on the user's name, or on the time of day the password
is to be entered--anything that is likely to vary from user to user.
The input to the one-way function is obtained by combining the
password with the salt. As usual, the corresponding output of the one-way
function is stored in the password file under the user's name. The
salt is also stored along with the output.
When the user later tries
to log in and supplies her name and password, the system looks up the
user's name in the password file and determines the corresponding
salt. The system then combines the salt with the password provided by
the user, and applies the one-way function to the combination. The
system compares the result to the value stored in the password file.
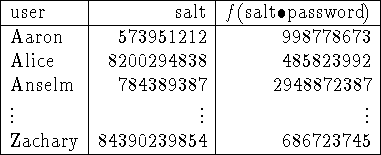
Figure 3: In a still more secure system, a salt is selected for each
user, and the one-way function is applied to a combination of the salt
and the password. Note that the output of the one-way function is
different for Alice and Zachary even though they have the same password.
Lisa Eckstein
Thu Nov 21 01:20:27 EST 1996
